Till now we have heard of ransomware’s targeted computers files will be encrypted, in this scenario users are allowed to login to the Operating System but won’t be able to open encrypted files. The newly discovered PETYA Crypto-Ransomware has crossed one more step and it overwrites the MBR itself to lock users out of their computers.
Petya is still distributed via email. Victims would receive an email tailored to look and read like an applicant applying for a job in a company. It would present users with a hyperlink to Dropbox storage location, which would let users download the above said user’s CV.
The file downloaded is actually a self-extracting executable which will unleash the trojan into the system.
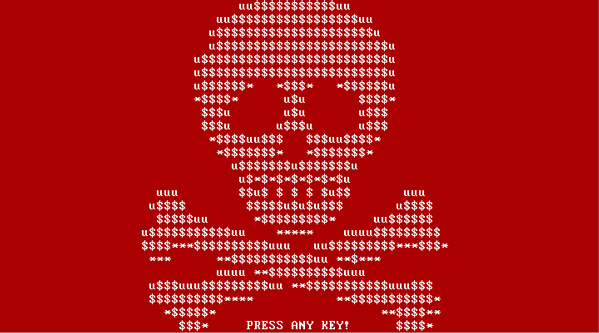
Once executed, Petya overwrites the MBR of the entire hard drive, causing windows to crash and display a blue screen. When the user tries to reboot the system the modified MBR will stop him to boot into the operating system, and will be greeted with an ASCII skull and an ultimatum: pay up with a certain amount of bitcoins or lose access to your files and computer.
Fig1: Petya’s red skulls-and-crossbones warning
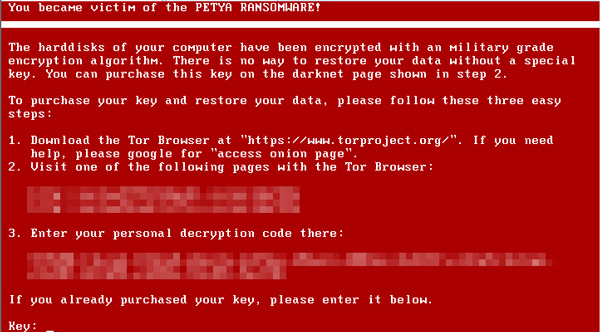
This modified MBR even disable booting to safe mode also. The user is then given explicit instructions on how to do this, just like any crypto-ransomware currently making the rounds: a list of demands, a link to the Tor Project and how to get to the payment page using it, and a personal decryption code.
Fig 2: Petya’s decryption and ransom payment instructions