Web Service Definition Language in short WSDL is an XML format for describing network services as a set of endpoints operating on messages containing either document-oriented or procedure oriented information.
WSDL is a
- XML document written to describe a web service.
- It specifies the location of the web service and the operations or methods the web service exposes.
A WSDL document uses the following elements in the definition of network services (Web services)
- Types – a container for data type definitions. This describes the data. The XML schema Language(Known as XSD also) is used for this purpose.
- Message – an abstract, typed definition of the data being communicated. The contains the information needed to perform the operation.
- Operation – an abstract description of an action supported by a service. This defines the actions and the way the message is encoded.
- Port Type – an abstract set of operations supported by one or more endpoints.
- Binding – a concrete protocol and data format specification for a particular port type. Defines the interface and the binding style.
- Port – a Single endpoint defined as a combination of a binding and a network address. It defines the address or the connection point to a web service.
- Service – a collection of related endpoints
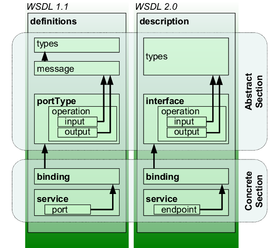
WSDL 1.2 has been renamed to WSDL 2.0, because of the major differences, like
- Removed message constructs.
- Operator overloading not supported.
- PortTypes renamed to interfaces.
- Ports renamed to interfaces.
- Added further semantics to the description language.
<?xml version="1.0" encoding="UTF-8"?>
<description xmlns="http://www.w3.org/ns/wsdl"
xmlns:tns="http://www.tmsws.com/wsdl20sample"
xmlns:whttp="http://schemas.xmlsoap.org/wsdl/http/"
xmlns:wsoap="http://schemas.xmlsoap.org/wsdl/soap/"
targetNamespace="http://www.tmsws.com/wsdl20sample">
<!-- Abstract type -->
<types>
<xs:schema xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns="http://www.tmsws.com/wsdl20sample"
targetNamespace="http://www.example.com/wsdl20sample">
<xs:element name="request"> ... </xs:element>
<xs:element name="response"> ... </xs:element>
</xs:schema>
</types>
<!-- Abstract interfaces -->
<interface name="Interface1">
<fault name="Error1" element="tns:response"/>
<operation name="Opp1" pattern="http://www.w3.org/ns/wsdl/in-out">
<input messageLabel="In" element="tns:request"/>
<output messageLabel="Out" element="tns:response"/>
</operation>
</interface>
<!-- Concrete Binding Over HTTP -->
<binding name="HttpBinding" interface="tns:Interface1"
type="http://www.w3.org/ns/wsdl/http">
<operation ref="tns:Get" whttp:method="GET"/>
</binding>
<!-- Concrete Binding with SOAP-->
<binding name="SoapBinding" interface="tns:Interface1"
type="http://www.w3.org/ns/wsdl/soap"
wsoap:protocol="http://www.w3.org/2003/05/soap/bindings/HTTP/"
wsoap:mepDefault="http://www.w3.org/2003/05/soap/mep/request-response">
<operation ref="tns:Get" />
</binding>
<!-- Web Service offering endpoints for both bindings-->
<service name="Service1" interface="tns:Interface1">
<endpoint name="HttpEndpoint"
binding="tns:HttpBinding"
address="http://www.example.com/rest/"/>
<endpoint name="SoapEndpoint"
binding="tns:SoapBinding"
address="http://www.example.com/soap/"/>
</service>
</description>
Example WSDL
